The Golden Pattern of Security: Distributed Cloud Computing
Part II
The first segment of this series took us on a deep dive into the concept of Unified Security Policies. We discovered how these policies, like the spirals of a nautilus shell, provide a stable and predictable security posture. For a recap of these foundational aspects, please refer to Part I of the Golden Pattern Series.
However, understanding the theory only marks the beginning of our journey. The real challenge lies in the practical application of these concepts. Hence, in this second part, I will explore the crucial domains of intricate encryption and identity and access management (IAM). For this purpose, I draw parallels with the Panama Canal, a symbol of secure, regulated passage and an engineering marvel.
The Panama Canal and Cloud Computing
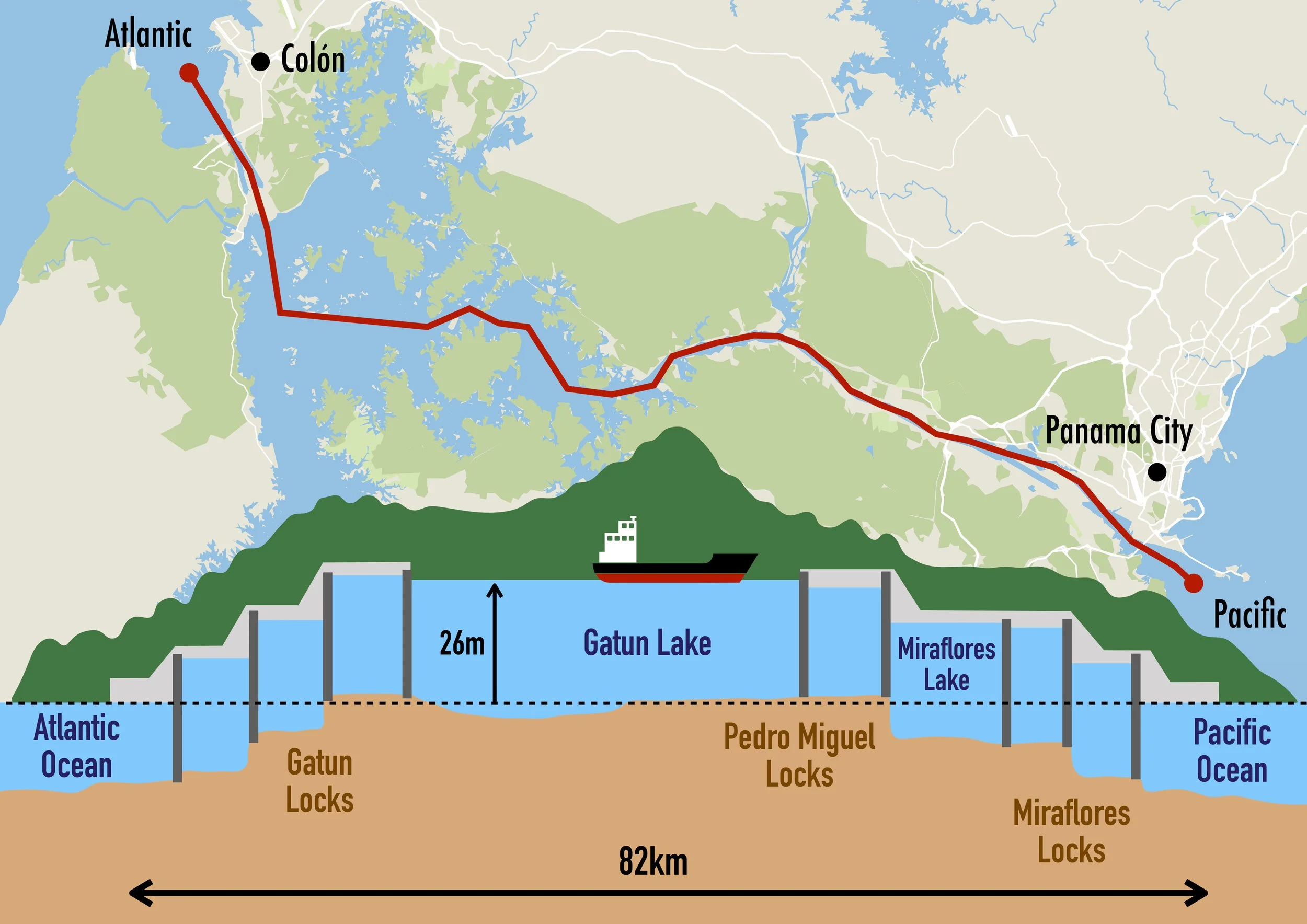
The Panama Canal, a marvel of modern engineering, stands as a testament to human ingenuity and perseverance in connecting two of the world’s greatest bodies of water. Completed in 1914, this monumental waterway has since played a crucial role in international maritime trade by facilitating direct passage between the Atlantic and Pacific Oceans. The canal’s innovative lock system is at the heart of its functionality, raising and lowering ships to navigate the varying sea levels, thereby avoiding the treacherous journey around Cape Horn.
The lock system is ingeniously designed with a series of water-filled chambers that employ the force of gravity to transition vessels between different elevations. As ships approach, these chambers function as water elevators, sequentially raising or lowering them to match the height differential between adjacent bodies of water. The process involves a delicate balance, using large valves to control the water flow and thus the ship’s elevation, without the need for pumps. Central to this process is Gatun Lake, an artificial yet vital component that provides a controlled expanse for ships to navigate through the canal’s midpoint.
Much like the Panama Canal’s lock system, which safely guides ships through its route, intricate encryption and IAM ensure secure data passage through the cloud. How can we strategically implement these vital aspects of cloud security? Let’s delve deeper.
Intricate Encryption: The Lock System for Distributed Cloud Computing
In the realm of distributed cloud computing, the role of AES encryption goes beyond just securing data. This ensures that as data traverses across multiple cloud environments, it remains impervious to unauthorized access and tampering. This is akin to how the Panama Canal’s lock system not only navigates ships through different sea levels but also provides a controlled and secure passage. In distributed cloud environments, where data often traverse various networks and servers, AES encryption acts as a critical safeguard, maintaining data integrity and confidentiality across disparate cloud platforms.
Identity and Access Management: Navigating Gatun Lake
Navigating the complexities of IAM in cloud computing can be likened to intricate navigation through Gatun Lake in the Panama Canal. Just as captains must skillfully maneuver their vessels through this expansive water body, IT professionals must adeptly manage access to cloud resources. The challenges in IAM, such as ensuring correct user permissions, preventing unauthorized access, and maintaining an audit trail, mirror the navigational challenges in Gatun Lake. Overcoming these challenges is crucial for maintaining a secure cloud environment, ensuring that only authorized personnel can access sensitive data, similar to how authorized vessels navigate through the strategic points of the Panama Canal.
Strategically implementing these critical components of cloud security—encryption and IAM—is as vital to cloud computing as the Panama Canal's lock and lake system is to global maritime navigation. Encryption ensures the safe passage of data, similar to the locks that ensure the safe passage of ships, while IAM systems provide a controlled environment for resource access, akin to the regulation of ship traffic in Gatun Lake.
Embracing Openness and Flexibility
As a Technology Evangelist, I strongly advocate the adoption of open-source encryption tools and IAM solutions in cloud computing. A vendor-agnostic approach, which is central to my philosophy, resonates with the transparency and robust security provided by open-source technologies. OpenSSL, for instance, is crucial for ensuring adaptability and strong security in the ever-changing cloud environment.
As I conclude Part II of the 'Golden Pattern of Security' series, my exploration into the nuances of Encryption and IAM in Distributed Cloud Computing, paralleled with the engineering marvel of the Panama Canal, has been both enlightening and foundational. In the upcoming Part III, I will delve deeper into the critical realms of Compliance Frameworks and Proactive Threat Detection. These areas are essential for strengthening the security fabric of distributed cloud environments. Stay tuned as I continue to navigate and unravel more layers of cloud security, to ensure robust and resilient digital ecosystems.